Do you want to know when an unknown computer (hacker?) has connected to your network? When hardware or software on any computer on your network is failing? When there are repeated login failures? Centralized logging and analysis can tell you all of that and so much more! Below I show you how I do centralized logging and how it helps me monitor and protect my network.
Table of Contents
Background
Because I work in IT, I’m very familiar with centralized logging. We’ve been doing it at companies I’ve worked at for years. Like at work, but on a much smaller scale, I have quite a few devices and applications I’m interested in monitoring for security. I’m also interested in stability and trying to be ahead of potential problems, but I want to focus on security in this article. Examples of devices and applications I monitor include:
- pfSense router (DNS, DHCP, and various security other functions).
- Managed switches (traffic flow).
- Wireless access points (guest wifi logins).
- Each of my PCs (firewall, administrative actions, logins).
This is a lot to monitor. Going to each machine and application and inspecting the logs would take a lot of time. I’m a time-strapped human and I don’t have that time. I looked for a some free to use systems for aggregating and processing logs and arrived at Graylog. Graylog is pretty easy to install in Docker or to install in Ubuntu.

Basic Graylog features
Graylog allows you to collect and process pretty much any kind of log file. It natively supports syslog and there are plugins that allow you to collect Windows EventLogs. If a log file is structured text you can configure Graylog to parse it. I use graylog to aggregate syslog files from all of my machines (router, PCs, access points, etc.). I also use it to collect snort data from my router/IDS firewall.
Once Graylog has this data you can configure dashboards and alerts based on processing rules and queries. I’ll give some examples of this later in this article. Other key features of Graylog include:
- Ability to save search queries.
- LDAP integration.
- REST API for integration into other parts of your IT Infrastructure. For instance, if you don’t like the dashboards in Graylog, and/or you are proficient in writing your own reports, you can use the REST API to make your own dashboards and reports in another system.
I am far from a Graylog expert. I basically just followed the online installation guide and a couple of pages in the documentation to make my setup. But even with that level of expertise, below are the 5 ways centralized logging with Graylog have helped my home network security.
1. Failed login detection
Windows event logs and syslogs contain records of authentication failures (such as entering a bad password). I set up an alert in Graylog that emails me whenever there are more than 3 unsuccessful authentication attempts in a minute. The alert will tell me which computer and send me a link to the log entries. Authentication failures can indicate someone is trying to break into your computer, so alerts for these events are a good line of defense.
2. Notification of new machines on my network
I assign all devices on my network an IP address using my router’s DHCP server. My router sends its logs to graylog. When any device I haven’t explicitly mapped joins my network I get an email alert from Graylog telling me the IP address, and a link to log entry. This way I know when anyone new connects to my network. Usually, this is just a new device I’ve bought and haven’t mapped, or sometimes…
3. Notification of users connecting to my guest wifi
Users who connect to my guest wifi (you have guest wifi, right?) aren’t already mapped to an IP via my DHCP server. So, I am also alerted when users connect to my guest wifi. Users who connect to my guest wifi get an IP in a specific range, which allows my alert to tell me the difference between a new machine, and someone connecting to my guest wifi. Graylog provides a tutorial and example for setting up streams and alert notifications.
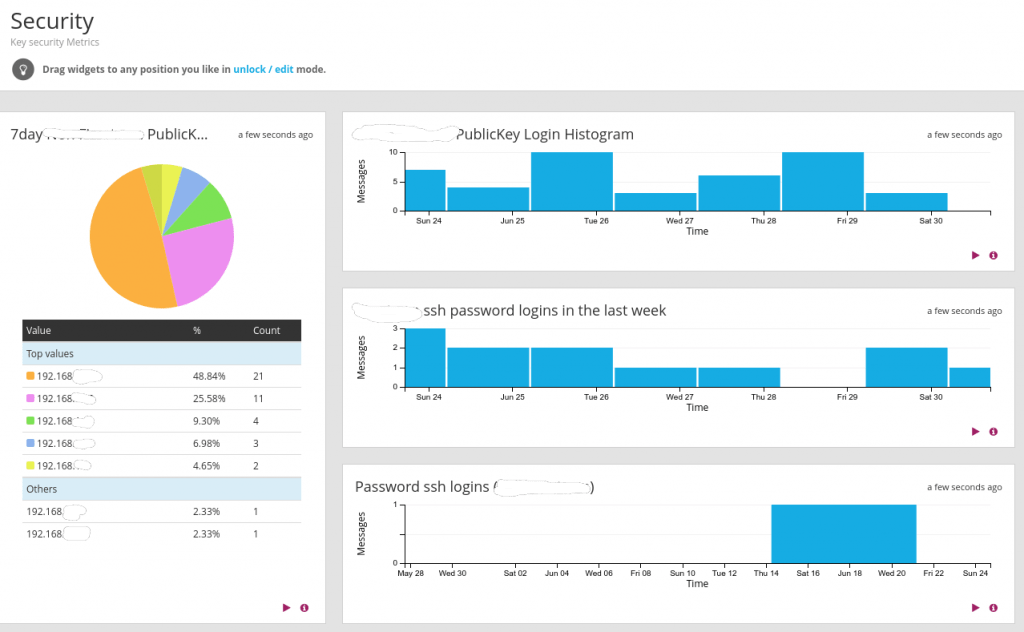
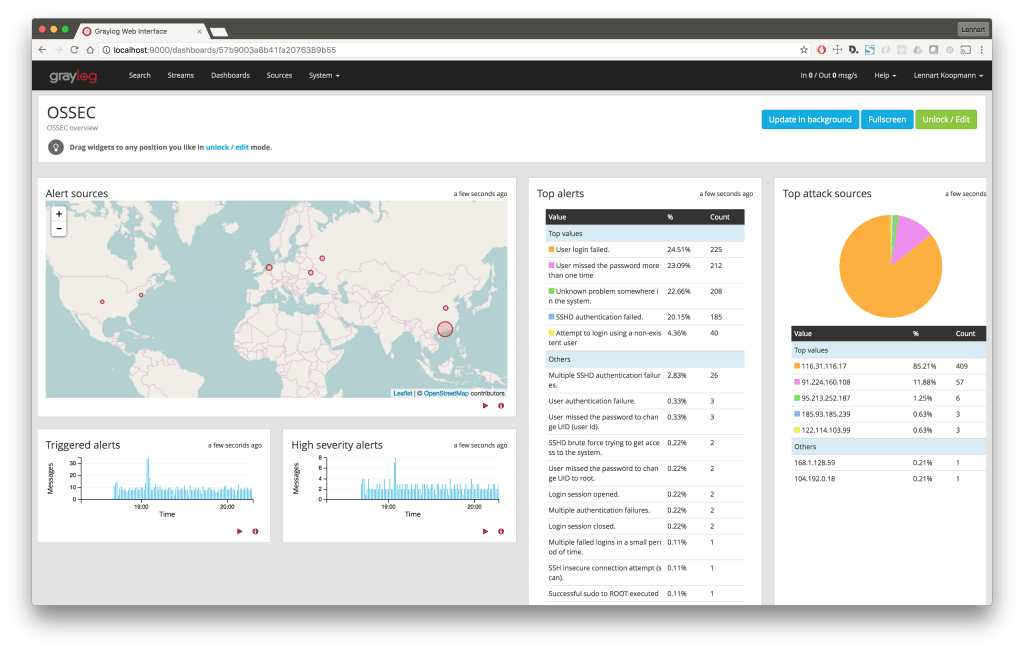
4. Setup dashboard with key security metrics
I wanted to play with the dashboard capabilities. As you can probably tell by my tinfoil hat, security is a very big deal to me. Of course, I set up a security dashboard. It tells me how many times someone logs into each of the machines, as well as a graph of login failures. All of this information is filterable by IP address and presented in charts that I can drill down into. For kicks, I also keep a histogram of how many security-related messages are in all of the aggregated logs. It’s a ton!
5. Ability to search for particular events
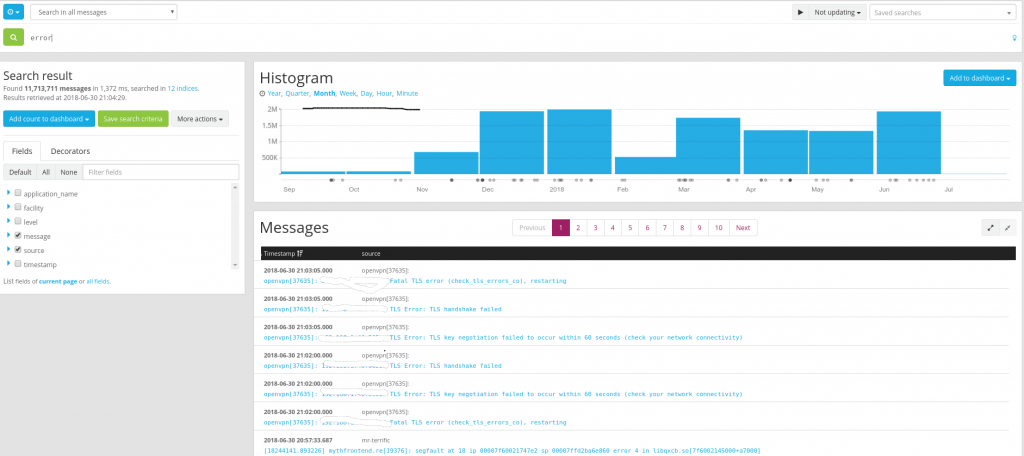
Sometimes things go wonky on my network, or things happen and I have no idea why. Often part of my troubleshooting involves looking through the logs. Graylog has a powerful search interface that allows me to search through my logs and track down what has happened. I’ve used this to help understand why some of my applications have crashed, or PCs rebooted, to investigate unusual traffic in my network, and other strange behavior on my network. I can use pretty complicated or simple searches, allowing me to narrow things down by IP, date range, program, and many more factors.
Final Thoughts
So far I’ve been pretty happy with Graylog. It didn’t take long to set up and provides me with valuable information when I need it. Additionally, if you use Docker, make sure you are centralizing your container logs. I’ve only scratched the surface of its capabilities.
You can also learn more about protecting yourself and your family online in my book The Personal Cybersecurity Manual: How Anyone Can Protect Themselves from Fraud, Identity Theft, and Other Cybercrimes.
Are any of you doing centralized logging at home? What tools are you using? Would you like to learn more about how to implement Graylog? Let me know in the comments.
If interested, I have more security tips here.


