
Email plays a crucial part in our daily communications, but it can cause damage to our systems as well. Do you know that around 90% of people are attacked via email? Yes, that is right. Phishing is a cybersecurity attack that uses calls, emails, or texts. Hackers use phishing to gain access to your sensitive information, ask you to open malicious links, and more.
The primary purpose of this attack is to steal users’ information like login details, credit card numbers, financial details, personal details, etc. Many people don’t know much about phishing attacks and how they work. But don’t worry because in this article, I will guide you through everything about it and how you can prevent it.
Table of Contents
What is a Phishing Attack?
As the name indicates, a phishing attack is a technique used by hackers to get your personal information via emails, calls, and text messages. These attacks ask recipients to open unknown links that can install malware on their systems. As a result, hackers can get all your details and even freeze your system. Not only does it damage individuals, but it can damage companies too. Some of the key characteristics of phishing attacks include:
- Email Phishing (Attack is done using email)
- Smishing (SMS Phishing)
- Spear Phishing (Mostly done to organizations)
- Vishing (Voice phishing)
- Pharming (Manipulates DNS – Domain Name Servers)
- Credential Harvesting (Gathers username and passwords)
- And more!
Phishing attacks are not limited to individuals; large organizations, tech companies, and different businesses can also become the victims of phishing attacks.
Editor’s Note: Phishing attacks are one of the top 10 personal cybersecurity threats you should be aware of.
How Phishing Attacks Work and How to Recognize Them
A phishing attack is divided into three different phases:
- The Bait
- The Hook
- The Attack
In the bait phase, the attacker uses a spoofing technique and sends a message via email, SMS, voicemail, etc. to one or more recipients simultaneously. Through the communication, cybercriminals collect information about the individual or the company. Common examples of attacks include free coupons, messages saying there are issues with your accounts, invoices, free government refunds, etc. This is sometimes called clickbait.
In the hook phase, the victim believes the communication is from a trusted source. Once the victim clicks the link, they will be redirected to a fake website where hackers can quickly get their sensitive data (e.g., login credentials, identity information, financial account numbers, etc.). If the communication contains any attachments, it will likely install a malicious code that can infect the device.
The final stage is the attack, where the scammer gets access to your account or uses the information to steal your identity. Using this data, the hacker attacks your organization or personal accounts.
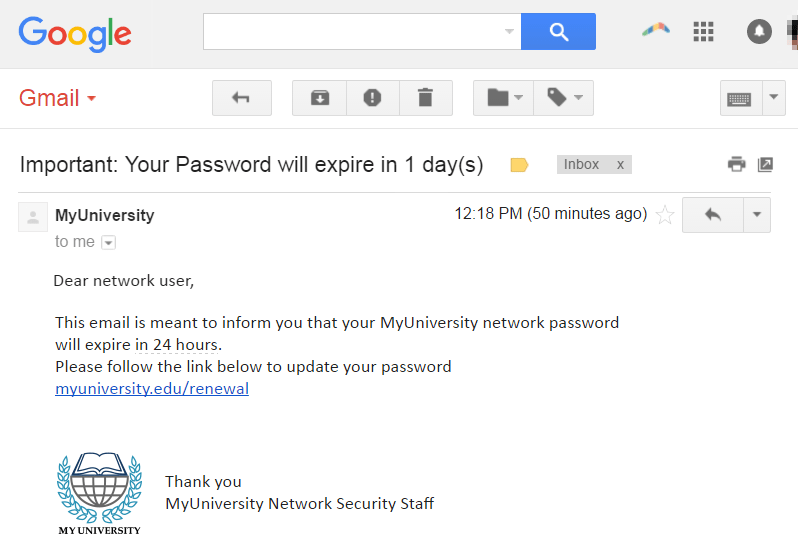
So, this is how a phishing attack works. Below is an image you can see to get an idea about the message you will most likely get from the hackers.
Top Ways to Prevent a Phishing Attack
Now that you clearly understand phishing attacks, it’s time to learn how to prevent them. To mitigate these attacks, users and enterprises can take the following steps.
- Two-Factor Authentication: Enabling 2FA can provide an extra layer of security to your accounts and counter phishing attacks. So, if the hacker tries to log in to your accounts, they need multiple details and/or devices to login.
- Use Complex Passwords: Users should not add names, numbers, or other details in their passwords, as including your name can make your password more susceptible to brute force attacks. So, keeping personal information out of your passwords is generally a good practice to enhance security. Pick a long passphrase (at least 15 characters) that is easy for you to remember but hard for others to guess
- Install Spam Filters: Installing robust spam filters is critical in protecting your email inbox from malicious and unwanted emails. These filters use various techniques to identify and categorize emails as spam or legitimate. Many email providers have spam filters you can tweak.
- Pay Attention to URLs: Most scammers will ask you to click the links, so before clicking them, pay attention to the URL, as it will have a misspelled domain name or extra subdomains. For example, uol.edu/renewal will be written as uol.edurenewal.com.
- Download Advanced Antivirus and Anti-Malware Programs: Install and regularly update your trusted antivirus and anti-malware programs to help prevent phishing attacks. Bitdefender, Norton, NordVPN, McAfee, and Total AV are the top antivirus programs you can use to detect cyberattacks.
- Educate Yourself and Your Family: Learn how to recognize phishing emails. Educating yoursel is an ideal way to learn about phishing attacks.
How HomeTechHacker can Help You Stop Phishing Attacks
HomeTechHacker provides many resources to help you stop phishing attacks.
- Learn how to protect yourself from data breaches that can lead to increased phishing attacks.
- Enroll in Personal Cybersecurity Protection, an online course that walks you step-by-step how to protect yourself from cybercriminals of all kinds.
- Purchase The Personal Cybersecurity Manual, which contains information anyone can follow to keep hackers and other cybercriminals at bay.
- Learn how to secure your home network, especially your Wi-Fi, to help limit damage if you are the victim of a phishing attempt.
- We also have an article about protecting yourself and loved ones from cybercriminals.
Ash Brooks is a freelance tech writer who has written over a thousand articles for various tech companies and blogs. She occasionally writes articles for HomeTechHacker.



